What Is Cybersecurity Mesh?

Their report states:
“By 2024, organizations adopting a cybersecurity mesh architecture will reduce the financial impact of security incidents by an average of 90%.”
What does this mean for you and your organization?
Cybersecurity mesh – definition
A cybersecurity mesh is a system of networking components that work together to create a secure environment. The term “mesh” refers to the way the components are interconnected, creating a barrier against unauthorized access or interference.


A cybersecurity mesh architecture (CSMA) uses a network of nodes to protect an organization’s data and infrastructure. Each node in the network is connected to the others and works together to identify and respond to threats. A CSMA uses a holistic, end-to-end security strategy.
This means that it takes into account all potential attack vectors and defends against them accordingly. By using a cybersecurity mesh, organizations can reduce the chance of being breached, as well as the financial impact of a breach.
The need for a new model
The traditional cybersecurity approach used to be based on the perimeter security model in which security and surveillance systems were set up at the perimeter of the network. The threats were mitigated as they entered a network. Now that networks are decentralized, workers are remote, and infrastructures are moved to multi-cloud environments, the concept of security has changed. Essentially, the perimeter-based security model does not suit the needs of the modern world.
The answer to these problems is the “Zero Trust” architecture – a security model that does not rely on predefined trust levels. In a Zero Trust security model, all users and devices are treated in the same manner, regardless of whether they’re inside or outside the corporate network. The goal of a Zero Trust security model is to secure data by making sure that only authorized users have access to it, regardless of their location. To do this, all traffic is monitored and inspected for malicious activity, and all users are required to authenticate themselves before they can access any data.
However, there are also some challenges associated with using a Zero Trust security model. For example, it can require more resources to monitor all traffic and authenticate all users. With a growing number of tools and systems, it can be chaotic to manage and tie together all the data. The ESG (Enterprise Strategy Group) reports that organizations use between 25 and 49 security tools from various vendors. Multiple security tools and multi-cloud environments need to be managed in a controlled way that allows interoperability. This is how the concept of cybersecurity mesh architecture (CSMA) was born.
Main concepts
Unlike the traditional cybersecurity models, the CSMA allows for having highly scalable and interoperable systems. Gartner names four foundational layers that build such architectures:
- Security Analytics and Intelligence – tools that combine logs, and analyze and alert anomalies
- Distributed Identity Fabric – tools for identity and access management (IAM)
- Consolidated Policy and Posture Management – tools that manage endpoints and devices policies in a centralized manner
- Consolidated dashboards – tools for detailed monitoring that allow for easy and fast incident response
Benefits of CSMA
The benefits of a cybersecurity mesh include:
- Improved detection and response to threats
- Reduced complexity and cost
- Increased flexibility and agility
- Improved security posture
Organizations that are considering a cybersecurity mesh should assess their current security architecture and identify gaps that could be addressed by this approach. They should also consider the resources required to implement and operate a cybersecurity mesh.
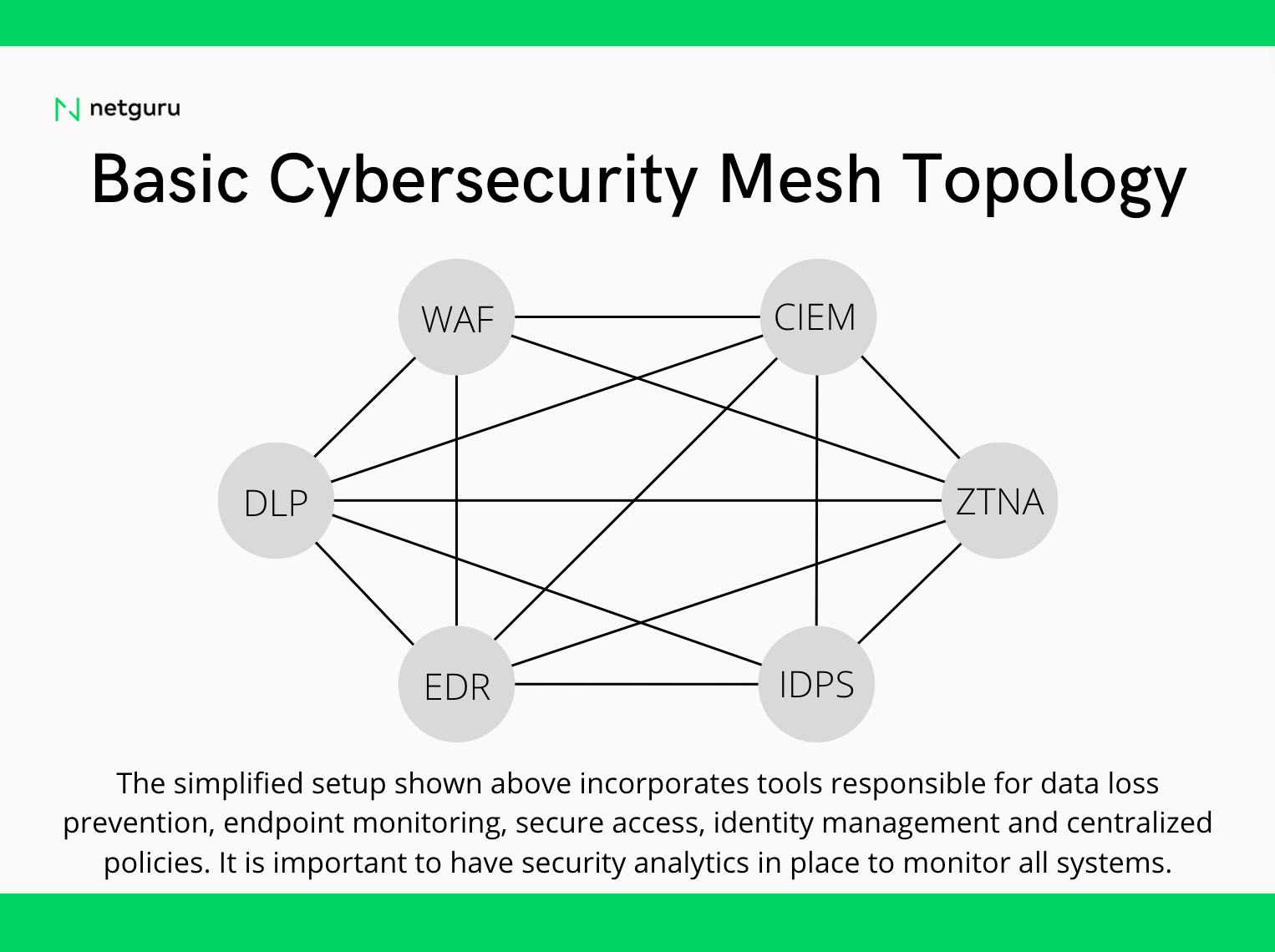
Components of a cybersecurity mesh
A cybersecurity mesh is a network of devices that work together to protect an organization from cyberattacks. Each device in the network is connected to the others and shares information about threats. This way, the network can identify and respond to attacks more quickly and effectively.
In order to properly defend against all possible attack vectors, a cybersecurity mesh must have several key components. These components work together to create a comprehensive security strategy that can defend against even the most sophisticated attacks.
- The first component of a cybersecurity mesh is a firewall. This is designed to protect your network from external threats. Firewalls can be hardware devices, software programs, or both. When a firewall detects an unauthorized connection, it blocks it. This helps to prevent attackers from getting into a network.
- The second component of a cybersecurity mesh is an intrusion detection and prevention system. Intrusion detection and prevention systems (IDPS) are devices that detect and prevent attacks. They work by analyzing network traffic and looking for patterns that indicate an attack. If an IDPS detects an attack, it can take action to stop it, such as blocking the connection or sending an alert.
- The third component of a cybersecurity mesh is a SIEM. Security information and event management (SIEM) systems are devices that collect and store data about security events. This data can be used to identify trends and track attacks. SIEM systems can also generate alerts if they detect suspicious activity.
- The fourth component of a cybersecurity mesh is an email security gateway. This gateway filters your email traffic for spam and malware. It also blocks phishing emails that could lead to data breaches.
- The fifth component of a cybersecurity mesh is endpoint security. This security solution protects your endpoints, such as laptops and smartphones, from malware and other threats. It also includes features like device management and data loss prevention to keep your endpoint data safe.
- The sixth component of a cybersecurity mesh is data loss prevention. This solution helps you prevent sensitive data from being leaked outside your organization. It includes features like data classification and encryption to keep your data safe.
- Another component of a cybersecurity mesh is identity and access management. This solution manages user identities and controls access to systems and data. It includes features like single sign-on and multifactor authentication to keep your systems secure.
By implementing these seven components, you can create a comprehensive security strategy that can defend against all types of cyberattacks. A properly implemented cybersecurity mesh will reduce the financial impact of security incidents by an average of 90%.
The complete cybersecurity mesh architecture, as shown in the Gartner report, consists of multiple services – not just the ones listed above. Yet, we have to keep in mind that the model has to be tailored to a company's needs. Not all businesses need to have all existing security tools to be secure.
A proper Zero Trust implementation has to cover the need for security monitoring, analytics, logging, as well as having a centralized policies and tools for identity and access management. Some companies might choose to deploy CIEM (Cloud Infrastructure Entitlements Management) for the purpose of managing identities in their multi-cloud environment, others might rely on their cloud IAM tools. As long as the four foundational layers are covered, your infrastructure is secure.
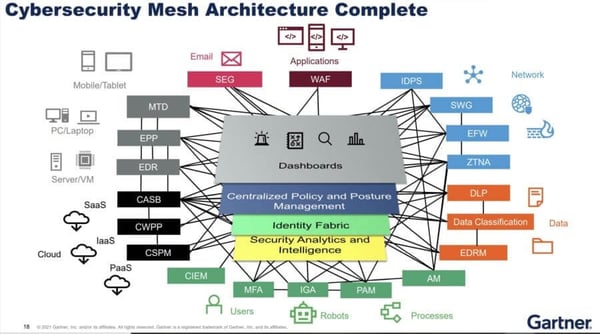
Cybersecurity mesh architecture (Source: Gartner)
Future of a cybersecurity mesh
Cybersecurity mesh is an emerging technology that promises to revolutionize the way we think about security. Google developed their BeyondCorp framework back in 2009, yet we had to wait for over a decade to see the popularization of Zero Trust.
As more organizations adopt this architecture, we will likely see a significant reduction in the number and severity of cyberattacks.







