iOS Security Analysis with MobSF

MobSF has many security testing options and has really great potential. There was one problem though, it only supported Objective-C for iOS code analysis.
After some brainstorming, we decided to contribute to MobSF and implement Swift support for source code analysis. Together with the creator of MobSF, Ajin Abraham, we did it! Swift source code analysis is now available in MobSF. This codestory will show you how MobSF works and how you can integrate it with your CI.
How does MobSF work?
Some of the security issues can be represented as regex or string. For example, you can find usage of weak hashes like MD5 with “CC_MD5”; MobSF looks for such patterns. Unfortunately, we can’t handle all security issues in this way, so please keep in mind that MobSF won’t replace real security reviews. You can, however, use it to check some of the issues or support the security review process.
What does MobSF check?
We analysed the OWASP Mobile Application Security Verification Standard and OWASP Mobile Security Testing Guide to extract as many patterns as we could. To see all Swift checks, please take a look in the swift_rules and common_rules files. You can also check out the objc_rules file for Objective-C checks. You can find binary analysis rules in the api_rules file.
The screenshot of the detected rule: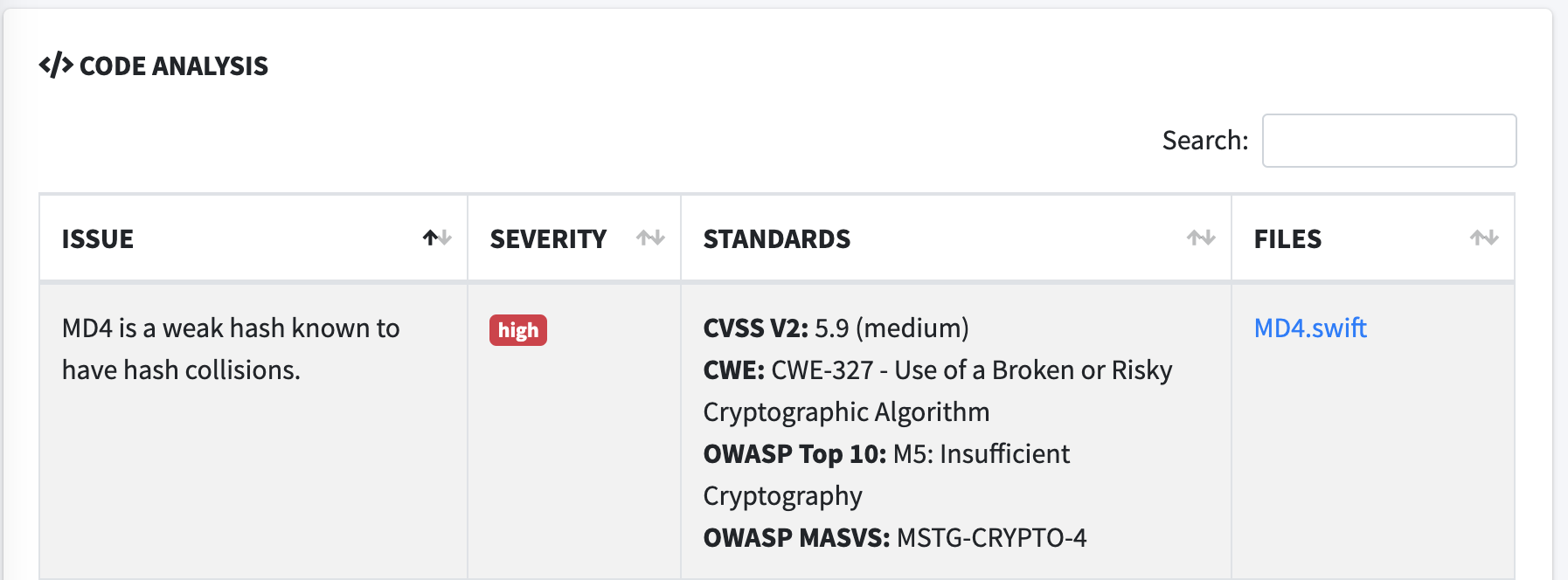
Installation
The easiest way to run MobSF is through Docker. It won’t support dynamic analysis, but it is only available for Android. If you have Docker installed and running, you can run MobSF with these commands:
docker pull opensecurity/mobile-security-framework-mobsf
# Static Analysis Only
docker run -it -p 8000:8000 opensecurity/mobile-security-framework-mobsf:latest
You can now access the MobSF web interface via your web browser, it will have the address http://localhost:8000/
If you don’t want to use Docker or you need Android dynamic analysis, please follow the steps in the documentation to run MobSF.
iOS code analysis requirements
To use iOS source code analysis, we need to meet some requirements. If you want to upload iOS source code, it has to be zipped. In the root folder of your zip, it has to contain the “*.xcodeproj” file. Another requirement is to have an Info.plist file in the zip. After meeting these requirements, you are good to upload the zip file.
Note: This codestory covers iOS source code analysis, if you would like to use binary analysis, use an archived ipa file instead of a zipped project.
Local usage
So you have MobSF running locally. Open MobSF with a web browser and drag your zipped source code. After a few seconds, you will receive the report.
Integration with Bitrise
Bitrise integration requires a few steps:
- Host MobSF.
- Add the zipping script to your repository.
- Configure the bitrise.yml to upload the source code to MobSF.
Host MobSF
MobSF has API implementation, so you can host it and use the API to interact with it. I’m not going to show you how to host it, the instructions are available in the MobSF repository. This tutorial requires hosted MobSF in order to integrate it with the Bitrise.
Zipping script
In order to analyze the source code of the app, it has to be zipped. I have created a script preparing and zipping the repository, you can find it here. Add it to your repository to access it from Bitrise. You can run it in two ways:
Zip diff files
Uploading and analyzing a big project with a lot of external libraries may take a lot of time. How can we save this time? If we create a pull request, we may want to scan only the difference between those branches. To extract the difference from pull requests, I have created the zip_diff_files function. It will zip only necessary files with xcodeproj and Info.plist. The zip will be named mobsf_files.zip and it will be available in the root directory.
function zip_diff_files() {
# Copy diff files to mobsf_files directory.
DIFF_FILES="$(git diff --name-only $TO_BRANCH..$FROM_BRANCH)"
FILES_ARRAY=($(echo $DIFF_FILES | tr " " "\n"))
mkdir mobsf_files
cp ${FILES_ARRAY[@]} ./mobsf_files
# Copy xcodeproj.
xcproj_file=$(find . -name "${PROJECT_NAME}.xcodeproj")
cp -r $xcproj_file ./mobsf_files
# Copy Info.plist.
plists="$(find . -name 'Info.plist')"
cp $plists ./mobsf_files
# Create zip.
cd ./mobsf_files
zip -r mobsf_files.zip .
cd ..
cp ./mobsf_files/mobsf_files.zip ./mobsf_files.zip
# Remove previously created files.
rm -rf ./mobsf_files
}
To run this function you need to pass project name, source branch, and destination branch:
sh prepare_mobsf.sh ProjectName $source_branch $destination_branch
Zip whole project
To send the whole project source code, we need to collect the project source code and copy xcodeproj to the root directory of the project. The script has a function to that that:
function zip_project() {
# Copy xcodeproj to RootDirectory
xcproj_file=$(find . -name "${PROJECT_NAME}.xcodeproj")
cp -r $xcproj_file ./
# Create zip
zip -r mobsf_files.zip .
}
To run this function you just need to provide the project name.
sh prepare_mobsf.sh ProjectName
bitrise.yml
To configure the project with Bitrise, we need to add functions calling the script and uploading the zip file. You can find those scripts in the repository or below. Remember to change projectName to the right one.
Upload project diff.
mobSF-check-diff:
steps:
- script:
inputs:
- content: |
#!/bin/bash
sh prepare_mobsf.sh ProjectName $BITRISE_GIT_BRANCH $BITRISEIO_GIT_BRANCH_DEST
after_run:
- upload-mobSF
Upload the whole project.
mobSF-check-project:
steps:
- script:
inputs:
- content: |
#!/bin/bash
sh prepare_mobsf.sh ProjectName
after_run:
- upload-mobSF
Send Zip to MobSF step
upload-mobSF:
steps:
- script:
inputs:
- content: |
#!/bin/bash
curl -F "file=mobsf_files.zip" mobsf.yourhost.com/api/v1/upload -H "Authorization:$MOBSF_API_TOKEN"
As you can see, upload-mobSF requires MOBSF_API_TOKEN, you should add it to the Bitrise secrets.
After adding those functions into your bitrise.yml, you can call them in the way that fits your needs. For example, when you create a pull request to master or release a branch.
Summary
As you can see, using MobSF is fairly easy locally. It requires more work to integrate it with CI, but it will check every change you make. I believe that we have gained a great Swift security analysis tool and our iOS team has gained a lot of knowledge. I encourage you to contribute; MobSF is a great tool and it can be even better with your help.
Ajin Abraham – We would like to thank you for MobSF and your great collaboration in Swift analysis support. 🎉